NIST 800-171

Save time
Reduce Costs
Increase Productivity
Reduce Risks
Ready to become NIST 800-171 compliant? Look no further than InfoGov.com. We offer comprehensive advisory services tailored to your needs, drawing on the expertise of our experienced consultants and cutting-edge artificial intelligence technology to efficiently identify information governance, risk, and compliance gaps.
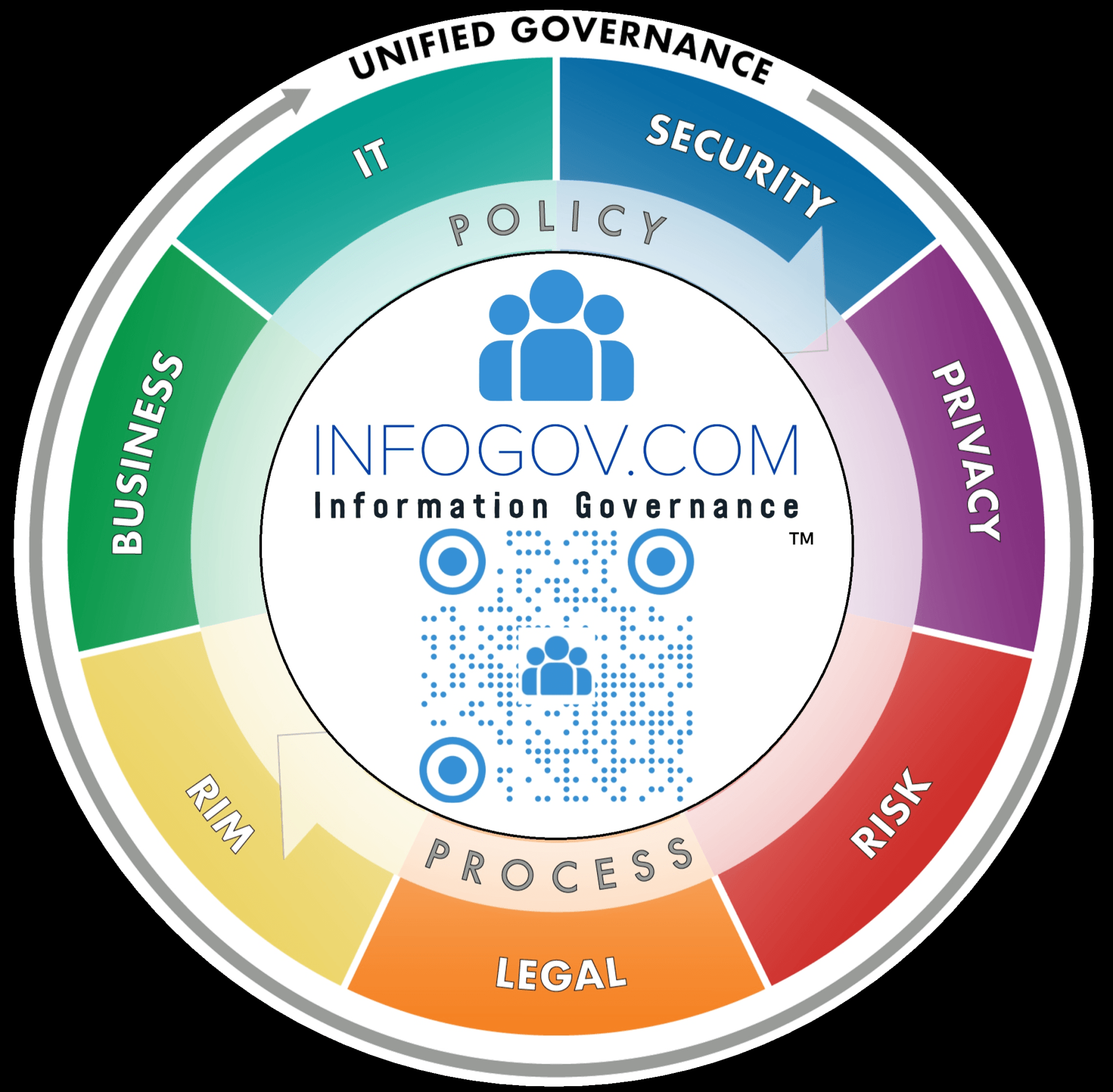
NIST 800-171 Compliance
At InfoGov.com, we understand that different departments in an organization may handle Controlled Unclassified Information (CUI) differently. That's why our expert consultants work directly with each business unit to evaluate their processes and identify gaps in compliance. For instance, we could help a defense contractor by assessing their engineering department's handling of CUI during the product development cycle, making sure they meet NIST 800-171 security standards with proper controls. Trust us to optimize your organizational approach to CUI management.
Improve Compliance
Optimize Security
InfoGov.com places a strong emphasis on security optimization. Our consultants evaluate existing security measures, such as access controls, encryption protocols, and incident response plans, to identify areas of improvement. By leveraging AI-based technology platforms, we can analyze vast amounts of data, identify potential vulnerabilities, and recommend appropriate security enhancements. As an example, we could assist a financial institution in implementing multi-factor authentication and encryption measures for securing financial transaction data.
Transform Records & Data
Enhance Information Technology
Our services extend to enhancing IT infrastructure to meet NIST 800-171 requirements. We assess the current IT environment, identify gaps in security controls, and propose technological solutions to address those gaps. For example, we could help a software development company implement secure coding practices and vulnerability scanning tools to protect their software source code.
Reassure Privacy
Reduce Risk
InfoGov.com's approach emphasizes risk reduction through programmatic evidence collection, control testing, and AI-driven risk assessments. By leveraging AI-based questionnaires and predictive risk assessments, we identify potential vulnerabilities and prioritize risk mitigation efforts. For example, we could help a government contractor assess the risk associated with their supply chain partners and establish controls to mitigate potential threats.
We're here to assist.
In summary, InfoGov.com offers comprehensive advisory services to assist clients in becoming NIST 800-171 compliant. Through our consultants' expertise and AI-based strategic partner technology platforms, we can efficiently identify gaps in information governance, risk, and compliance. By focusing on each client's specific needs, such as lines of business, legal compliance, security optimization, records and data transformation,
a b c d e f g h i j k l m n o - Do not remove from template!!! it is important to support different fonts

Slide title
Write your caption hereButton
Slide title
Write your caption hereButton
Slide title
Write your caption hereButton
Slide title
Write your caption hereButton
Slide title
Write your caption hereButtonSlide title
Write your caption hereButton
Slide title
Write your caption hereButton
Slide title
Write your caption hereButton
Slide title
Write your caption hereButton-
Slide title
Write your caption hereButton 
Slide title
Write your caption hereButton
Slide title
Write your caption hereButton
Slide title
Write your caption hereButton
Slide title
Write your caption hereButton
Contact Us
We will get back to you as soon as possible.
Please try again later.





