Our Services
Get Compliant, Be Compliant, Stay Compliant.
| 〇 | ◔ | ◑ | ◕ | ⬤ |
|---|
| InfoAdvisor℠ Solutions & Services: | Info Risk Analysis | Information Governance Workshop | InfoAdvisor℠ Discovery | InfoClave™ Secure Enclave as a Service | VIP Advisory Services |
|---|---|---|---|---|---|
| Description | Risk Score & Report | Business Workshop & Continuing Education (CE, CPE, CLE) | Initial Data & Technology Insights Engagement | End User Sensitive Information Secure Enclave: Discovery, Implementation, Configuration, & Reporting | Custom Advisory Consulting, Training, Coaching, Remediation & Implementation |
| Client Participants | ✔ Up to 2 Client Attendees | ✔ Up to 8 Client Attendees | ✔ Up to 10 Client Interviews | ✔ 10+ Client Users | ✔ Custom |
| Audience | ✔ C-Suite, Core Business leaders, HR, Legal, Compliance, Records/Data, IT, Security, Risk | ✔ C-Suite, Core Business leaders, HR, Legal, Compliance, Records/Data, IT, Security, Risk | ✔ C-Suite, Core Business leaders, HR, Legal, Compliance, Records/Data, IT, Security, Risk | ✔Sensitive Data Business Users, HR, Legal, Compliance, Records/Data, IT, Security, Risk | ✔ C-Suite, Core Business leaders, HR, Legal, Compliance, Records/Data, IT, Security, Risk |
| Deliverables | ✔ Free Internet Risk Score ✔ Paid Report High Level Risk Remediation Plan | ✔ Roadmap ✔ Worksheets & Certificates ✔ Internet Risk Score ✔ Paid\ Report High Level Risk Remediation Plan | ✔ Detailed Analysis ✔ Detailed Risk Remediation Roadmap ✔ Playbooks | ✔ Detailed Analysis ✔ Detailed Risk Remediation Roadmap ✔ Project Plan ✔ Features: VPN, SSO, Encryption, Data Loss Prevention, Compliance Monitoring & Reporting | ✔ Detailed Analysis ✔ Detailed Risk Remediation Roadmap ✔ Multi-Tiered Project Plans, KPI/KRI Reports, Workshops, Vendor Management, & More |
| Advisors | 1-2 | 1-2 | 1-2+ | 1-3+ | 3+ |
| Tech Consultants | 0 | 0 | 1-2 | 1-2 | 3+ |
| People Analysis | - | Yes | Yes | Yes | Yes |
| Process Analysis | - | Yes | Yes | Yes | Yes |
| Technology Analysis | Yes | Yes | Yes | Yes | Yes |
| Technology Implementation | - | - | - | Yes | Yes |
| Software Licensing | - | - | - | Yes | Yes |
| Contract | - | - | Yes | Yes | Yes |
| Business | ✅ | ✅ | ✅ | ✅ | ✅ |
| IT | ✅ | ✅ | ✅ | ✅ | ✅ |
| Security | ✅ | ✅ | ✅ | ✅ | ✅ |
| Privacy | ✅ | ✅ | ✅ | ✅ | ✅ |
| Risk | ✅ | ✅ | ✅ | ✅ | ✅ |
| Legal | ✅ | ✅ | ✅ | ✅ | ✅ |
| Records/Data | ✅ | ✅ | ✅ | ✅ | ✅ |
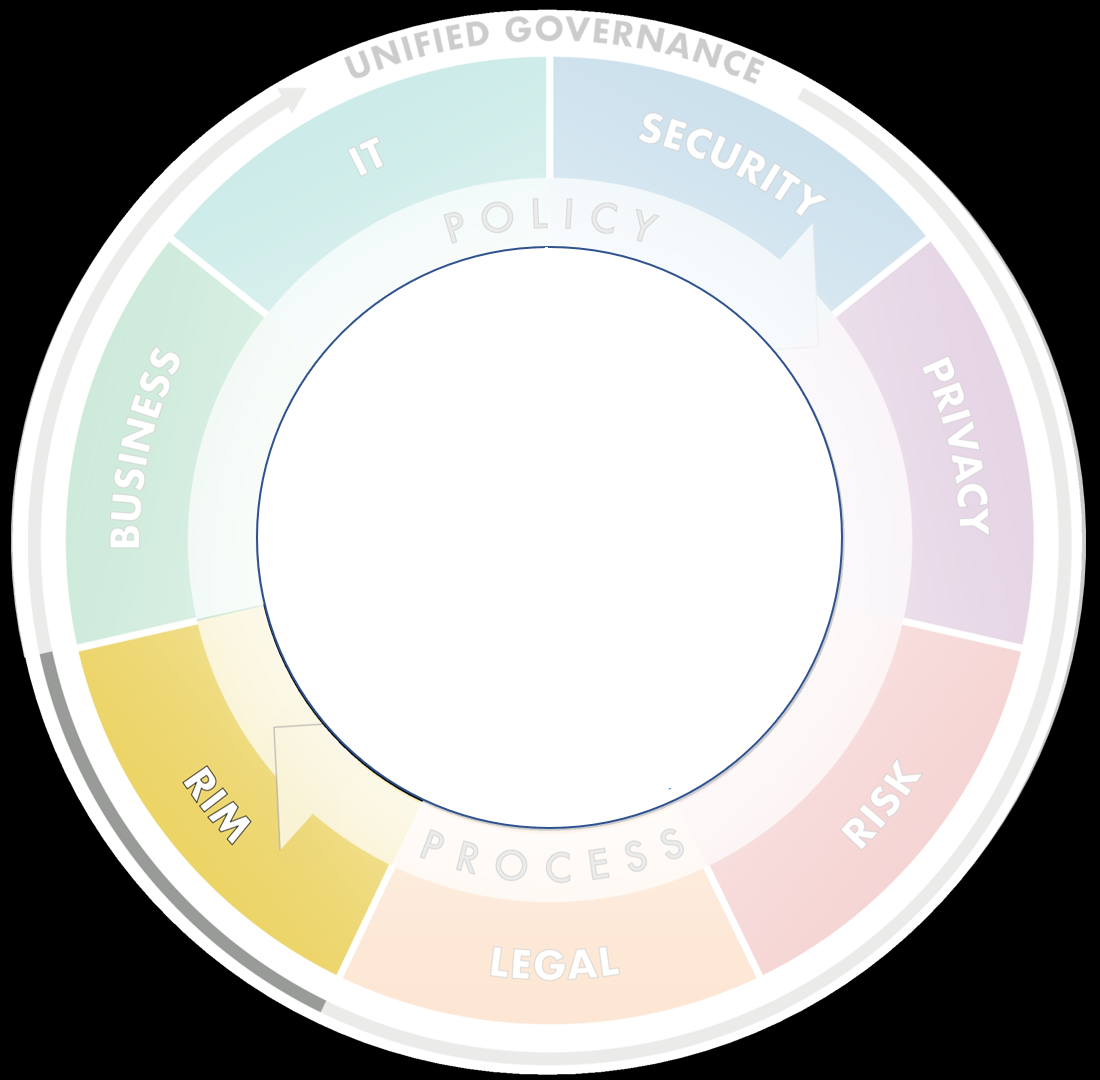
| GOVERN | ✅ | ✅ | ✅ | ✅ | ✅ |
| IDENTIFY | ✅ | ✅ | ✅ | ✅ | ✅ |
| PROTECT | - | ✅ | ✅ | ✅ | ✅ |
| DETECT | - | - | ✅ | ✅ | ✅ |
| RESPOND | - | - | - | ✅ | ✅ |
| RECOVER | - | - | - | - | ✅ |
| Timeframe | 24 Hours | 3 Days | 3 Weeks (Min.) | 4-6 Weeks (Min.) | 3-6 Months (Min.). |
| Pricing | FREE | $$$ | $,$$$ | $$,$$$ | $$,$$$+ /yr | $$$,$$$+ |
| 〇 | ◔ | ◑ | ◕ | ⬤ |
|---|
People: INFOADVISOR™
 Schedule a Call
Schedule a CallInfo Risk Analysis & Workshops
Risk and efficiency analysis of data protection, privacy policies, and compliance measures.
For B2B small and medium businesses (SMBs) and B2C across various industries with specific compliance needs.
Process: INFOGOV.com™
 Schedule a Call
Schedule a CallAdvisory Services
Expert-guided services for building and maintaining information governance programs.
For large and enterprise businesses in highly regulated industries such as legal, healthcare, financial services, critical infrastructure sectors and more.
Technology: INFOCLAVE™
 Schedule a Call
Schedule a CallSecure Enclaves as a Service
Managed Secure Enclave Services with Governance, Risk, Compliance Monitoring & Controls.
For businesses needing secure daily business workflows and document management before or after a breach or audit.
Info Risk Analysis
Don't know your company's information risk profile? Start with a Risk Score, Report, & Cyber Insurance Quote:
- Free Internet Risk Score
- Cyber Insurance Quote
- Paid Report High Level Risk Remediation Plan
- Within 24 Hours
Information Governance Workshop
Unsure of the information risks inside your company? Conduct a Business Workshop to prioritize remediation and also earn Continuing Education (CE, CPE, CLE) credits:
- Information Governance Roadmap
- C-Suite, Core Business leaders, HR, Legal, Compliance, Records/Data, IT, Security, Risk
- Worksheets & Certificates Internet Risk Score Report
- High Level Risk Remediation Plan
- 1 week lead time
- 3 Days
$$$$
InfoClave™ Secure Enclave as a Service
Need to protect sensitive data workflows immediately? Leverage our All-in-one Information Protection Platforms:
- All in one Information Protection Platforms for Users. Sensitive Information: Discovery, Implementation, Configuration, & Reporting
- 10+ Client Users
- Sensitive Data Business Users, HR, Legal, Compliance, Records/Data, IT, Security, Risk
- Detailed Analysis
- Detailed Risk Remediation Roadmap
- Project Plan
- Features: VPN, SSO, Encryption, Data Loss Prevention, Compliance Monitoring & Reporting
- Available immediately
- 1-3 Weeks (Min.) Deployment
$$$$$+ /yr.
InfoAdvisor℠ Discovery
Need assistance with a new or existing project? Let us optimize your processes with an Initial Data & Technology Insights Engagement:
- Initial Data & Technology Insights Engagement
- Up to 10 Client Interviews
- C-Suite, Core Business leaders, HR, Legal, Compliance, Records/Data, IT, Security, Risk
- Detailed Analysis
- Detailed Risk Remediation Roadmap
- Playbooks
- 1 week lead time
- 3 Weeks (Min.) Engagement Length
$$$$$
VIP Advisory Services
To hire an individual or team of experts for more complex projects and programs, choose our Custom Advisory Services:
- Custom Advisory Consulting, Training, Coaching, Remediation & Implementation
- C-Suite, Core Business leaders, HR, Legal, Compliance, Records/Data, IT, Security, Risk
- Detailed Analysis
- Detailed Risk Remediation Roadmap
- Multi-Tiered Project Plans
- KPI/KRI Reports
- Workshops
- Vendor Management
- 1-2 week lead time
- 2 Months (Min.) Engagement Length
$$$$$$+
Advisory Program Management
- Collaborate with experienced Subject Matter Experts
- Utilize expert contractors from multi-domains and industries
- Procure staff assistance in augmentation
- Ensure certified and background checked staff
- Providing all resource levels for any duration of time*
*Based on contracted agreement

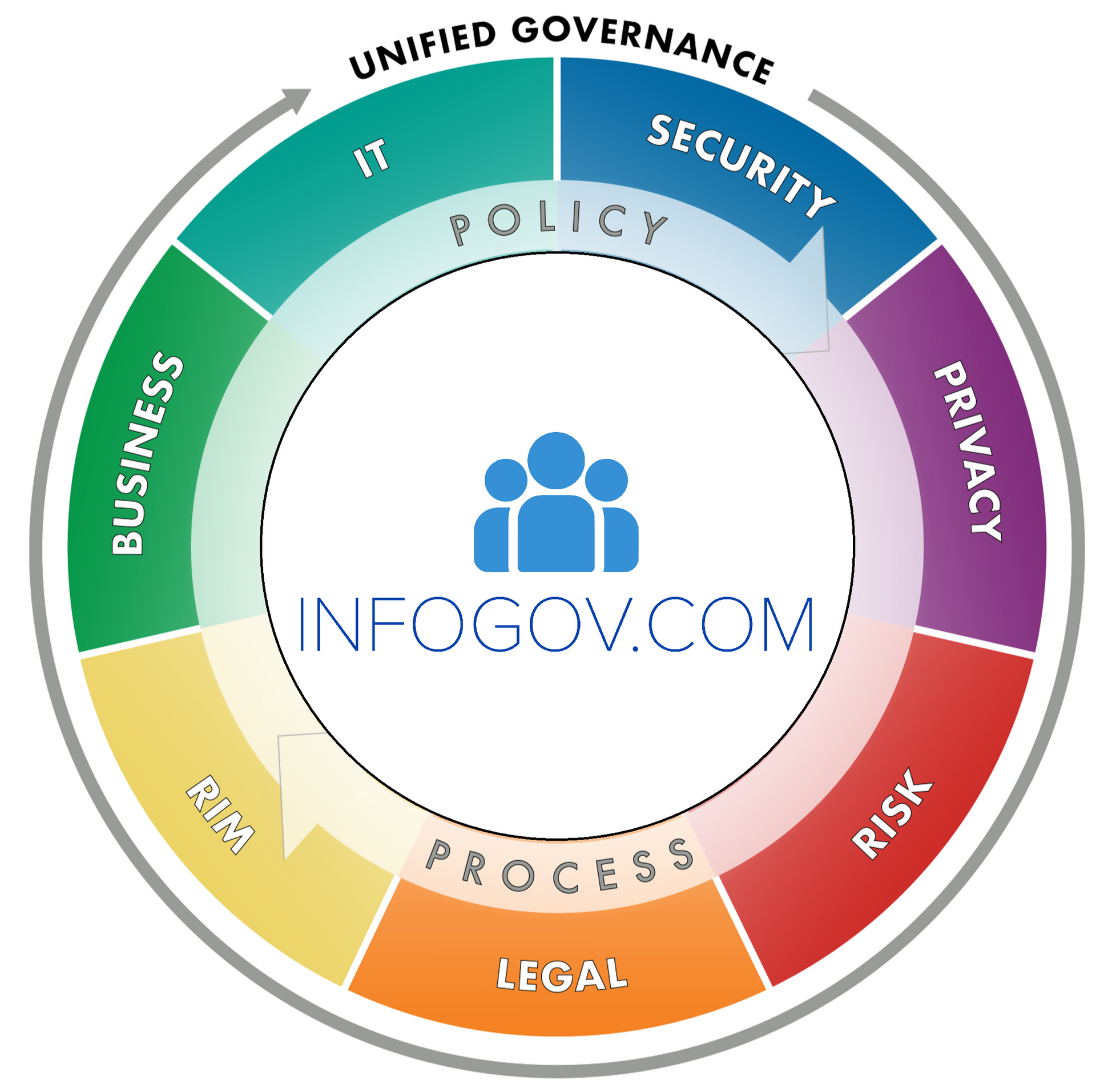
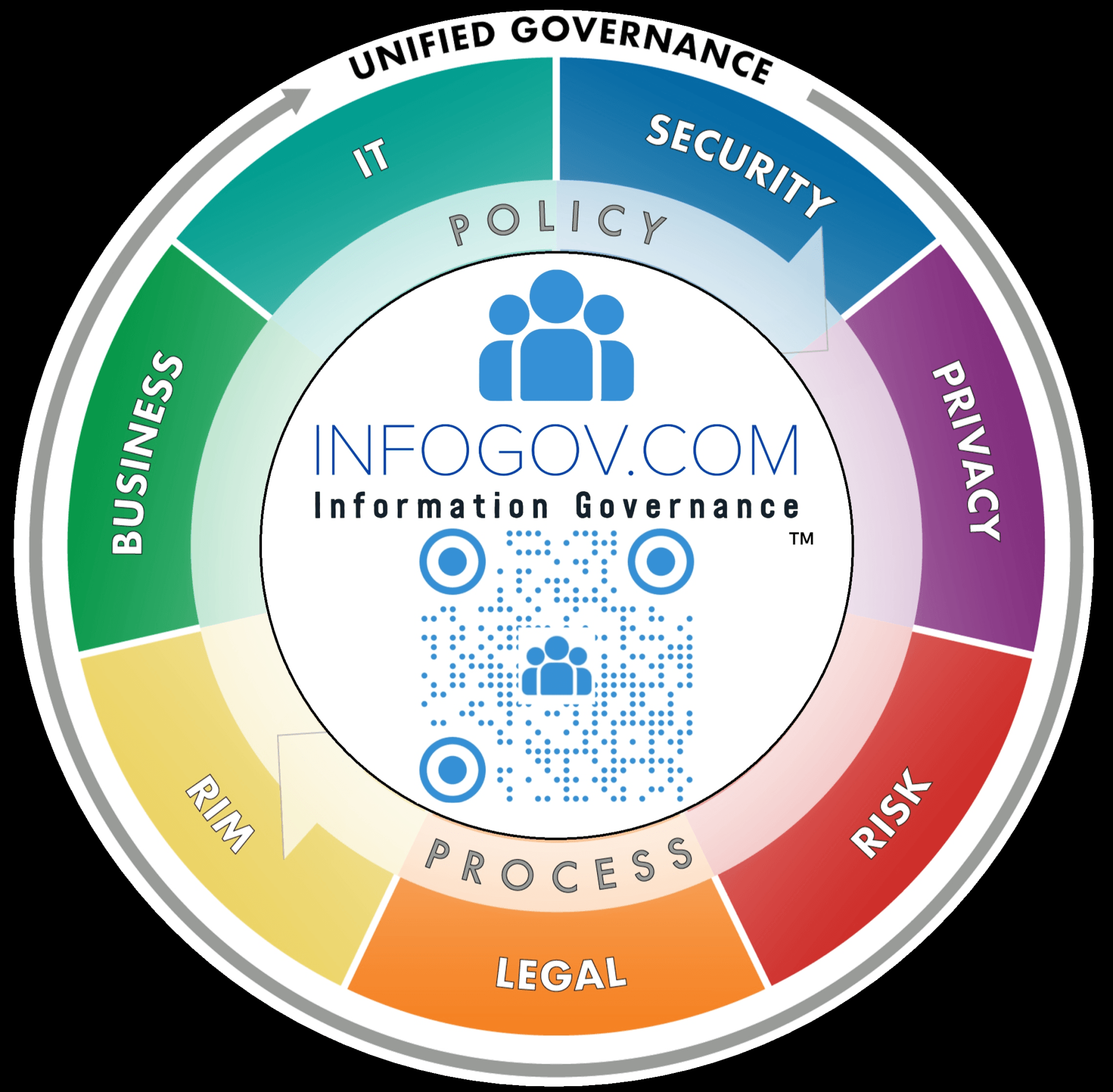
InfoGov Council Partners
InfoGov Council Partners have experience, and interdisciplinary backgrounds in multiple lines of business, Legal & Compliance, Security, Records Information Managent (RIM) & Data Governance, IT, Privacy, and Risk.
Line of Business
Our business coaches have information management experience in various lines of busines, understand the importance of research and training to create streamlined processes and facilitate productivity.
Legal & Compliance
Our Legal and Compliance professionals guide businesses to better understand, and comply with applicable regulations in day to day operations through research and training.
Security & Cybersecurity
Our Security and Cybersecurity professionals research and provide training on policies, roles, and technologies to protect business sensitive data, digital assets, and documents from external and internal threats.
RIM & Data Governance
Our Data Governance, Digital Asset, and Records Information Management professionals manage classification, availability, usability, quality, and integrity ensuring appropriate lifecycle managment.
Information & Technology
Our Information Technology professionals train business clients how to strategically leverage technical infrastructure and automation to support Information Governance activities.
Privacy
Our Privacy professionals understand how businesses share, collect, and store data ensuring compliance with applicable regulations on the local, state, federal and country level through research and training.
Government Policy
Our Government Professionals engaged in local, federal, and international government policy making, understand the value of research, and training to bring forth efficiencies serving the needs of the public and your organization.
RECEIVE A CUSTOM QUOTE
Contact Us
We will get back to you as soon as possible
Please try again later
TURNING KNOWLEDGE INTO ACTION
-
INFO RISK ANALYSIS
START -
IT STRATEGY
START -
SECURITY STRATEGY
Write your caption hereSTART -
PRIVACY STRATEGY
Write your caption hereSTART -
RISK STRATEGY
START -
POLICY STRATEGY
START -
RECORDS & DATA STRATEGY
Write your caption hereSTART -

INFOGOV WORKSHOP
Write your caption hereSTART -

IT ANALYSIS
Write your caption hereSTART -

SECURITY ANALYSIS
Write your caption hereSTART -

PRIVACY ANALYSIS
Write your caption hereSTART -

RISK ANALYSIS
Write your caption hereSTART -

POLICY ANALYSIS
Write your caption hereSTART -

RECORDS & DATA ANALYSIS
Write your caption hereSTART -

DIGITAL TRANSFORMATION
Write your caption hereSTART -

IT AUTOMATION
Write your caption hereSTART -

SECURITY REMEDIATION
Write your caption hereSTART -

PRIVACY REMEDIATION
Write your caption hereSTART -

RISK REMEDIATION
Write your caption hereSTART -

LEGAL E-DISCOVERY
Write your caption hereSTART -

RECORDS & DATA DISCOVERY
Write your caption hereSTART -

DIGITAL TRAINING
Write your caption hereSTART -

IT TRAINING
Write your caption hereSTART -

SECURITY TRAINING
Write your caption hereSTART -

PRIVACY TRAINING
Write your caption hereSTART -

RISK TRAINING
Write your caption hereSTART -

LEGAL TRAINING
Write your caption hereSTART -

RECORDS & DATA TRAINING
Write your caption hereSTART -

REPORT AUTOMATION
Write your caption hereSTART -

IT REPORTING
Write your caption hereSTART -

SECURITY REPORTING
Write your caption hereSTART -

PRIVACY REPORTING
Write your caption hereSTART -

RISK REPORTING
Write your caption hereSTART -

COMPLIANCE REPORTING
Write your caption hereSTART -

RECORDS & DATA REPORTING
Write your caption hereSTART -

DIGITAL RESEARCH
Write your caption hereSTART -

IT RESEARCH
Write your caption hereSTART -

SECURITY RESEARCH
Write your caption hereSTART -

PRIVACY RESEARCH
Write your caption hereSTART -

RISK RESEARCH
Write your caption hereSTART -

LEGAL RESEARCH
Write your caption hereSTART -

RECORDS & DATA RESEARCH
Write your caption hereSTART
Get Compliant, Be Compliant, Stay Compliant.
| 〇 | ◔ | ◑ | ◕ | ⬤ |
|---|
| InfoAdvisor℠ Solutions & Services: | Info Risk Analysis | Information Governance Workshop | InfoAdvisor℠ Discovery | InfoClave™ Secure Enclave as a Service | VIP Advisory Services |
|---|---|---|---|---|---|
| Description | Risk Score & Report | Business Workshop & Continuing Education (CE, CPE, CLE) | Initial Data & Technology Insights Engagement | End User Sensitive Information Secure Enclave: Discovery, Implementation, Configuration, & Reporting | Custom Advisory Consulting, Training, Coaching, Remediation & Implementation |
| Client Participants | ✔ Up to 2 Client Attendees | ✔ Up to 8 Client Attendees | ✔ Up to 10 Client Interviews | ✔ 10+ Client Users | ✔ Custom |
| Audience | ✔ C-Suite, Core Business leaders, HR, Legal, Compliance, Records/Data, IT, Security, Risk | ✔ C-Suite, Core Business leaders, HR, Legal, Compliance, Records/Data, IT, Security, Risk | ✔ C-Suite, Core Business leaders, HR, Legal, Compliance, Records/Data, IT, Security, Risk | ✔Sensitive Data Business Users, HR, Legal, Compliance, Records/Data, IT, Security, Risk | ✔ C-Suite, Core Business leaders, HR, Legal, Compliance, Records/Data, IT, Security, Risk |
| Deliverables | ✔ Free Internet Risk Score ✔ Paid Report High Level Risk Remediation Plan | ✔ Roadmap ✔ Worksheets & Certificates ✔ Internet Risk Score ✔ Paid\ Report High Level Risk Remediation Plan | ✔ Detailed Analysis ✔ Detailed Risk Remediation Roadmap ✔ Playbooks | ✔ Detailed Analysis ✔ Detailed Risk Remediation Roadmap ✔ Project Plan ✔ Features: VPN, SSO, Encryption, Data Loss Prevention, Compliance Monitoring & Reporting | ✔ Detailed Analysis ✔ Detailed Risk Remediation Roadmap ✔ Multi-Tiered Project Plans, KPI/KRI Reports, Workshops, Vendor Management, & More |
| Advisors | 1-2 | 1-2 | 1-2+ | 1-3+ | 3+ |
| Tech Consultants | 0 | 0 | 1-2 | 1-2 | 3+ |
| People Analysis | - | Yes | Yes | Yes | Yes |
| Process Analysis | - | Yes | Yes | Yes | Yes |
| Technology Analysis | Yes | Yes | Yes | Yes | Yes |
| Technology Implementation | - | - | - | Yes | Yes |
| Software Licensing | - | - | - | Yes | Yes |
| Contract | - | - | Yes | Yes | Yes |
| Business | ✅ | ✅ | ✅ | ✅ | ✅ |
| IT | ✅ | ✅ | ✅ | ✅ | ✅ |
| Security | ✅ | ✅ | ✅ | ✅ | ✅ |
| Privacy | ✅ | ✅ | ✅ | ✅ | ✅ |
| Risk | ✅ | ✅ | ✅ | ✅ | ✅ |
| Legal | ✅ | ✅ | ✅ | ✅ | ✅ |
| Records/Data | ✅ | ✅ | ✅ | ✅ | ✅ |
| GOVERN | ✅ | ✅ | ✅ | ✅ | ✅ |
| IDENTIFY | ✅ | ✅ | ✅ | ✅ | ✅ |
| PROTECT | - | ✅ | ✅ | ✅ | ✅ |
| DETECT | - | - | ✅ | ✅ | ✅ |
| RESPOND | - | - | - | ✅ | ✅ |
| RECOVER | - | - | - | - | ✅ |
| Timeframe | 24 Hours | 3 Days | 3 Weeks (Min.) | 4-6 Weeks (Min.) | 3-6 Months (Min.). |
| Pricing | FREE | $$$ | $,$$$ | $$,$$$ | $$,$$$+ /yr | $$$,$$$+ |
| 〇 | ◔ | ◑ | ◕ | ⬤ |
|---|
Interested in our services? We’re here to help!
We want to know your needs exactly so that we can provide the perfect solution. Let us know what you want and we’ll do our best to help.
a b c d e f g h i j k l m n o - Do not remove from template!!! it is important to support different fonts

Slide title
Write your caption hereButton
Slide title
Write your caption hereButton
Slide title
Write your caption hereButton
Slide title
Write your caption hereButton
Slide title
Write your caption hereButtonSlide title
Write your caption hereButton
Slide title
Write your caption hereButton
Slide title
Write your caption hereButton
Slide title
Write your caption hereButton-
Slide title
Write your caption hereButton 
Slide title
Write your caption hereButton
Slide title
Write your caption hereButton
Slide title
Write your caption hereButton
Slide title
Write your caption hereButton
Contact Us
We will get back to you as soon as possible.
Please try again later.